Opening IT Excellence: Your Neighborhood Managed Provider
Opening IT Excellence: Your Neighborhood Managed Provider
Blog Article
Strategize and Scale WITh Proven IT Managed Solutions Approaches
In the busy landscape of modern-day business, the critical use of IT managed services has actually come to be a foundation for organizations intending to enhance functional efficiency and drive lasting growth. By carrying out tried and tested strategies customized to satisfy particular business needs, firms can browse the intricacies of modern technology while continuing to be active and affordable in their corresponding markets.
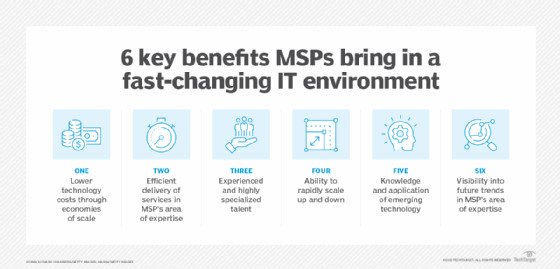
Advantages of IT Handled Provider
By outsourcing IT administration to a specialized carrier, businesses can touch into a wealth of proficiency and resources that would certainly otherwise be expensive to preserve internal. One of the vital advantages of IT Managed Solutions is proactive surveillance and maintenance of systems, which helps prevent possible concerns prior to they intensify right into significant problems.
Furthermore, IT Handled Services can offer access to the most up to date innovations and ideal practices without the need for continuous investment in training and infrastructure upgrades. This ensures that businesses remain affordable in a swiftly progressing technical landscape. In addition, by offloading routine IT tasks to a managed companies, interior IT groups can focus on strategic initiatives that drive development and development for the organization. Finally, the benefits of IT Managed Services are instrumental in simplifying operations, increasing efficiency, and eventually, driving organization success.
Key Strategies for Application
With an understanding of the substantial advantages that IT Managed Services deal, services can currently focus on applying vital methods to effectively incorporate these solutions right into their procedures - msp association of america. In addition, services have to establish clear interaction channels with their handled service provider to guarantee smooth partnership and timely issue resolution.
One more essential strategy is to prioritize cybersecurity actions. Information violations and cyber dangers pose considerable dangers to businesses, making safety and security a leading concern. Carrying out robust security procedures, normal tracking, and timely updates are essential actions in safeguarding delicate info and maintaining service connection.
In addition, organizations should develop solution level contracts (SLAs) with their handled company to define expectations, obligations, and efficiency metrics. SLAs aid in setting clear guidelines, guaranteeing accountability, and keeping service quality standards. By including these key techniques, organizations can leverage IT Took care of Services to improve operations, improve performance, and drive sustainable development.
Taking Full Advantage Of Efficiency Through Automation

Furthermore, automation allows real-time monitoring and data analysis, supplying important understandings for notified decision-making. By automating regular tracking tasks, companies can proactively attend to issues prior to they intensify, decreasing downtime and optimizing performance (msp association of america). In addition, automation can facilitate the smooth see combination of different systems and applications, improving cooperation and information flow across the organization
Ensuring Information Safety and Conformity
Information safety and security and compliance are extremely important issues for businesses running in the electronic landscape these days. With the enhancing quantity of sensitive data being stored and refined, guaranteeing durable security measures is crucial to guard versus cyber threats and abide by regulative demands. Applying extensive data safety practices involves encrypting data, developing access controls, on a regular basis upgrading software, and carrying out safety audits. Complying with policies such as GDPR, HIPAA, or PCI DSS is necessary to maintain and prevent pricey charges count check my blog on with clients. Managed IT providers play a crucial role in aiding businesses browse the complex landscape of information security and conformity. They supply competence in applying safety and security procedures, keeping an eye on systems for prospective breaches, and guaranteeing adherence to market policies. By partnering with a trustworthy managed companies, services can boost their data safety stance, alleviate threats, and show a commitment to securing the privacy and stability of their data properties.
Scaling IT Framework for Growth
Integrating scalable IT facilities options is crucial for helping with company growth and functional efficiency. As firms expand, their IT requires progress, needing facilities that can adapt to raised demands perfectly. By scaling IT facilities successfully, organizations can guarantee that their systems continue to be reliable, safe, and performant also as work expand.
One secret aspect of scaling IT framework for growth is the capacity to flexibly allot sources based on existing demands. Cloud computer solutions, for instance, deal scalability by allowing organizations to adjust storage space, refining power, and other sources as needed. This elasticity allows business to effectively take care of spikes in demand without over-provisioning resources throughout durations of lower activity.
Additionally, carrying out virtualization technologies can boost scalability by making it possible for the development of digital circumstances that can be conveniently copied or customized to suit changing work - msp association of america. By virtualizing web servers, storage space, and networks, companies can enhance resource utilization and simplify IT monitoring procedures, inevitably sustaining service development campaigns effectively
Verdict
Finally, implementing IT took care of solutions can bring countless advantages to an organization, such as increased performance, improved data safety and security, and scalability for growth. By complying with key techniques for execution, utilizing automation to optimize efficiency, and guaranteeing data safety and security and compliance, organizations can better plan and scale their IT infrastructure. It is essential for companies to evolve and adjust with technological check it out improvements to remain affordable in today's ever-changing landscape.
Report this page